Source
ghsa
### Impact SQL injection can occur when all of the following conditions are met: 1. The non-default simple protocol is used. 2. A placeholder for a numeric value must be immediately preceded by a minus. 3. There must be a second placeholder for a string value after the first placeholder; both must be on the same line. 4. Both parameter values must be user-controlled. e.g. Simple mode must be enabled: ```go // connection string includes "prefer_simple_protocol=true" // or // directly enabled in code config.ConnConfig.PreferSimpleProtocol = true ``` Parameterized query: ```sql SELECT * FROM example WHERE result=-$1 OR name=$2; ``` Parameter values: `$1` => `-42` `$2` => `"foo\n 1 AND 1=0 UNION SELECT * FROM secrets; --"` Resulting query after preparation: ```sql SELECT * FROM example WHERE result=--42 OR name= 'foo 1 AND 1=0 UNION SELECT * FROM secrets; --'; ``` ### Patches The problem is resolved in v4.18.2. ### Workarounds Do not use the simple protocol or do not place ...
LangChain through 0.1.10 allows ../ directory traversal by an actor who is able to control the final part of the path parameter in a load_chain call. This bypasses the intended behavior of loading configurations only from the hwchase17/langchain-hub GitHub repository. The outcome can be disclosure of an API key for a large language model online service, or remote code execution.
An issue was discovered in Cloud Native Computing Foundation (CNCF) Helm. It displays values of secrets when the --dry-run flag is used. This is a security concern in some use cases, such as a --dry-run call by a CI/CD tool. NOTE: the vendor's position is that this behavior was introduced intentionally, and cannot be removed without breaking backwards compatibility (some users may be relying on these values).
Cross Site Scripting (XSS) vulnerability in hexo-theme-anzhiyu v1.6.12, allows remote attackers to execute arbitrary code via the algolia search function.
An issue was discovered in phpseclib 1.x before 1.0.23, 2.x before 2.0.47, and 3.x before 3.0.36. An attacker can construct a malformed certificate containing an extremely large prime to cause a denial of service (CPU consumption for an isPrime primality check). NOTE: this issue was introduced when attempting to fix CVE-2023-27560.
An issue was discovered in phpseclib 1.x before 1.0.23, 2.x before 2.0.47, and 3.x before 3.0.36. When processing the ASN.1 object identifier of a certificate, a sub identifier may be provided that leads to a denial of service (CPU consumption for decodeOID).
Any SpiceDB cluster with any schema where a resource being checked has more than 65535 relationships for the same resource and subject type is affected by this problem. The issue may also lead to a panic rendering the server unavailable The following API methods are affected: - [CheckPermission](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.PermissionsService.CheckPermission) - [BulkCheckPermission](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.ExperimentalService.BulkCheckPermission) - [LookupSubjects](https://buf.build/authzed/api/docs/main:authzed.api.v1#authzed.api.v1.PermissionsService.LookupSubjects) #### Impact Permission checks that are expected to be allowed are instead denied, and lookup subjects will return fewer subjects than expected. #### Workarounds There is no workaround other than making sure that the SpiceDB cluster does not have very wide relations, with the maximum value being the maximum value of an 16-bit unsig...
### Impact Currently the exact Directus version number is being shipped in compiled JS bundles which are accessible without authentication. With this information a malicious attacker can trivially look for known vulnerabilities in Directus core or any of its shipped dependencies in that specific running version. ### Patches The problem has been resolved in versions 10.8.3 and newer ### Workarounds None
### Summary Security misconfiguration in edit configuration file API in dashboard component of ESPHome version 2023.12.9 (command line installation) allows authenticated remote attackers to read and write arbitrary files under the configuration directory rendering remote code execution possible. ### Details It is possible to abuse this path traversal vulnerability both in command line installation and Home Assistant add-on, but it is possible to read and write files only under the configuration directory. The vulnerability is present and exploitable in the command line installation, but it was not possible to confirm an impact in the home assistant add-on version. ### PoC <img width="482" alt="/edit?configuration=/config/.esphome/esphome.json" src="https://github.com/esphome/esphome/assets/115887876/d2da3180-976e-4bed-b4b9-35ac960a7fb4"> <br/> <img width="344" alt="/edit?configuration=/config/.esphome/build/test01/src/main.cpp (firmware for board named test01)" src="https://github...
### Impact Previously, budibase used a library called `vm2` for code execution inside the Budibase builder and apps, such as the UI below for configuring bindings in the design section. 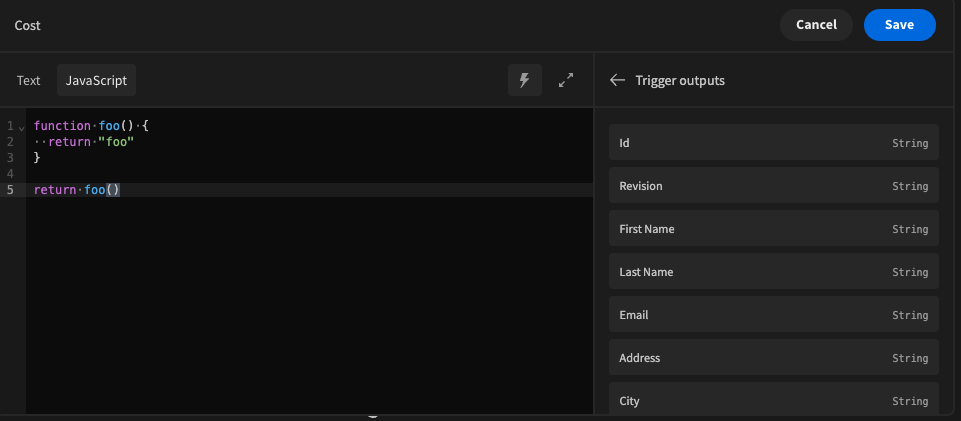 Due to a [vulnerability in vm2](https://github.com/advisories/GHSA-cchq-frgv-rjh5), any environment that executed the code server side (automations and column formulas) was susceptible to this vulnerability, allowing users to escape the sandbox provided by `vm2`, and to expose server side variables such as `process.env`. It's recommended by the authors of `vm2` themselves that you should move to another solution for remote JS execution due to this vulnerability. ### Patches We moved our entire JS sandbox infrastructure over to `isolated-vm`, a much more secure and recommended library for remote code execution in 2.20.0. This also comes with a performance benefit in the way w...