Source
ghsa
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 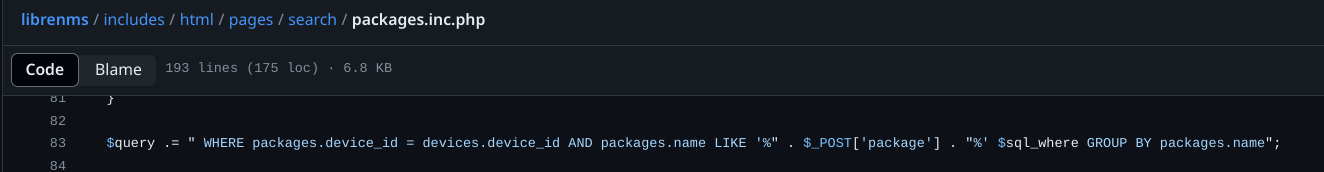 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
### Summary when jadx parses a resource file, there is an escape problem with the style file, which can overwrite other files in the directory when saving the decompile result. Although I don't think this vulnerability realizes path traversal in the true sense of the word , I reported it anyway ### Details I see that getResAlias does something with the filename. ```java private String getResAlias(int resRef, String origKeyName, @Nullable FieldNode constField) { ``` but type style will return the original filename directly. 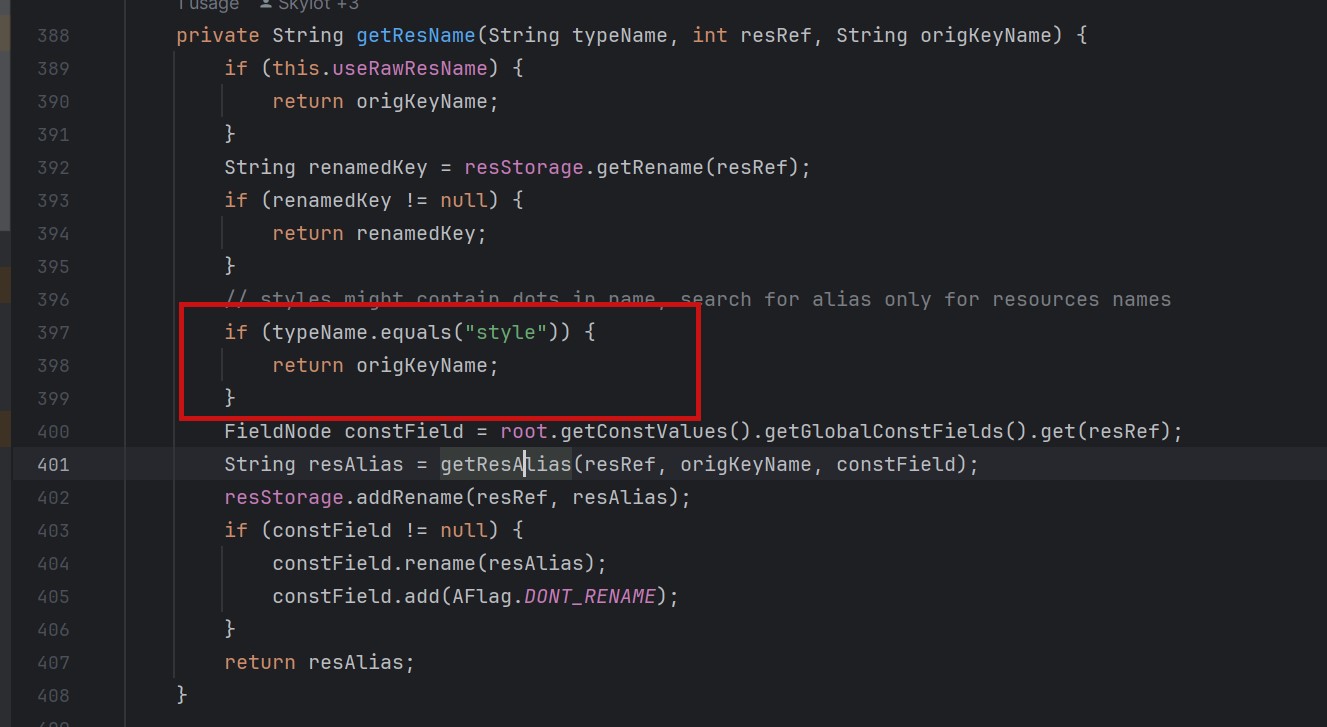 so our goal is to take a malicious file that was originally of type raw, modify its type to style, trick jadx into #### step1 create an android project using androidstudio and create a raw folder with the name attack_file_sayhiiiiiiiiiiiii, it doesn't matter what the content is! 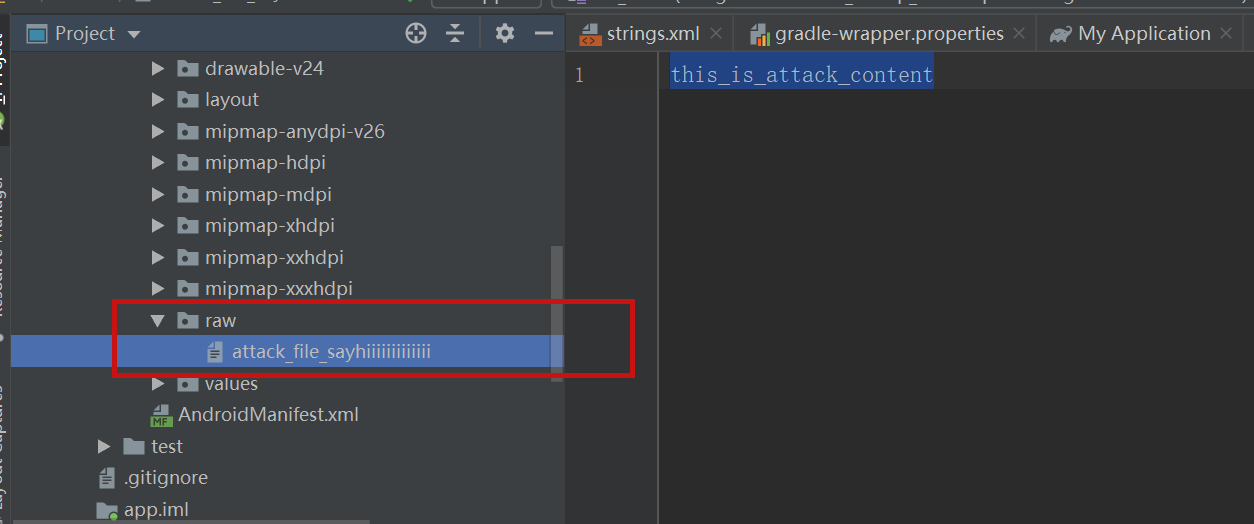 generate an initial APK #### s...
### Impact Under very specific conditions changes to a users groups may not have the expected results. The specific conditions are: * The file authentication backend is being used. * The [watch](https://www.authelia.com/configuration/first-factor/file/#watch) option is set to true. * The [refresh_interval](https://www.authelia.com/configuration/first-factor/introduction/#refresh_interval) is configured to a non-disabled value. * The users groups are adjusted by an administrator. * The user attempts to access a resource that their groups previously had access to but their new groups do not have access to. When these conditions are met administrators may find the changes are not taken into account by access control for longer than expected periods. While this may not necessarily be a security vulnerability it's security-adjacent and because of the unexpected nature of it and our dedication to a security-first culture we feel it's important to make users aware of this behaviour utiliz...
### Impact We have identified a local privilege escalation vulnerability in Ant Media Server which allows any unprivileged operating system user account to escalate privileges to the root user account on the system. This vulnerability arises from Ant Media Server running with Java Management Extensions (JMX) enabled and authentication disabled on localhost on port 5599/TCP. This vulnerability is nearly identical to the local privilege escalation vulnerability CVE-2023-26269 identified in Apache James. Any unprivileged operating system user can connect to the JMX service running on port 5599/TCP on localhost and leverage the MLet Bean within JMX to load a remote MBean from an attacker-controlled server. This allows an attacker to execute arbitrary code within the Java process run by Ant Media Server and execute code within the context of the “antmedia” service account on the system. ### Patches 2.9.0 ### Workarounds Remote the following parameters from antmedia.service file ```-Dcom....
Authentication Bypass by Spoofing vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.
Server-Side Request Forgery (SSRF) vulnerability in Apache HugeGraph-Hubble. This issue affects Apache HugeGraph-Hubble: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.
RCE-Remote Command Execution vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0 in Java8 & Java11 Users are recommended to upgrade to version 1.3.0 with Java11 & enable the Auth system, which fixes the issue.
Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting'/`XSS`) vulnerability in Apache Answer.This issue affects Apache Answer: before 1.3.0. XSS attack when user changes personal website. A logged-in user, when modifying their personal website, can input malicious code in the website to create such an attack. Users are recommended to upgrade to version [1.3.0], which fixes the issue.
Improper Certificate Validation vulnerability in Apache Airflow FTP Provider. The FTP hook lacks complete certificate validation in FTP_TLS connections, which can potentially be leveraged. Implementing proper certificate validation by passing context=ssl.create_default_context() during FTP_TLS instantiation is used as mitigation to validate the certificates properly. This issue affects Apache Airflow FTP Provider: before 3.7.0. Users are recommended to upgrade to version 3.7.0, which fixes the issue.
### Impact The application hangs when receiving a Host header with a value that `@hono/node-server` can't handle well. Invalid values are those that cannot be parsed by the `URL` as a hostname such as an empty string, slashes `/`, and other strings. For example, if you have a simple application: ```ts import { serve } from '@hono/node-server' import { Hono } from 'hono' const app = new Hono() app.get('/', (c) => c.text('Hello')) serve(app) ``` Sending a request with a Host header with an empty value to it: ``` curl localhost:3000/ -H "Host: " ``` The results: ``` node:internal/url:775 this.#updateContext(bindingUrl.parse(input, base)); ^ TypeError: Invalid URL at new URL (node:internal/url:775:36) at newRequest (/Users/yusuke/work/h/159/node_modules/@hono/node-server/dist/index.js:137:17) at Server.<anonymous> (/Users/yusuke/work/h/159/node_modules/@hono/node-server/dist/index.js:399:17) at Server.emit (node:events:514:2...