Tag
#android
Eight out of nine apps that people use to input Chinese characters into mobile devices have weakness that allow a passive eavesdropper to collect keystroke data.
By Waqas Popular keyboard apps leak user data! Citizen Lab reports 8 out of 9 Android IMEs expose keystrokes. Change yours & protect passwords! This is a post from HackRead.com Read the original post: Popular Keyboard Apps Leak User Data: Billion Potentially Exposed
### Summary when jadx parses a resource file, there is an escape problem with the style file, which can overwrite other files in the directory when saving the decompile result. Although I don't think this vulnerability realizes path traversal in the true sense of the word , I reported it anyway ### Details I see that getResAlias does something with the filename. ```java private String getResAlias(int resRef, String origKeyName, @Nullable FieldNode constField) { ``` but type style will return the original filename directly. 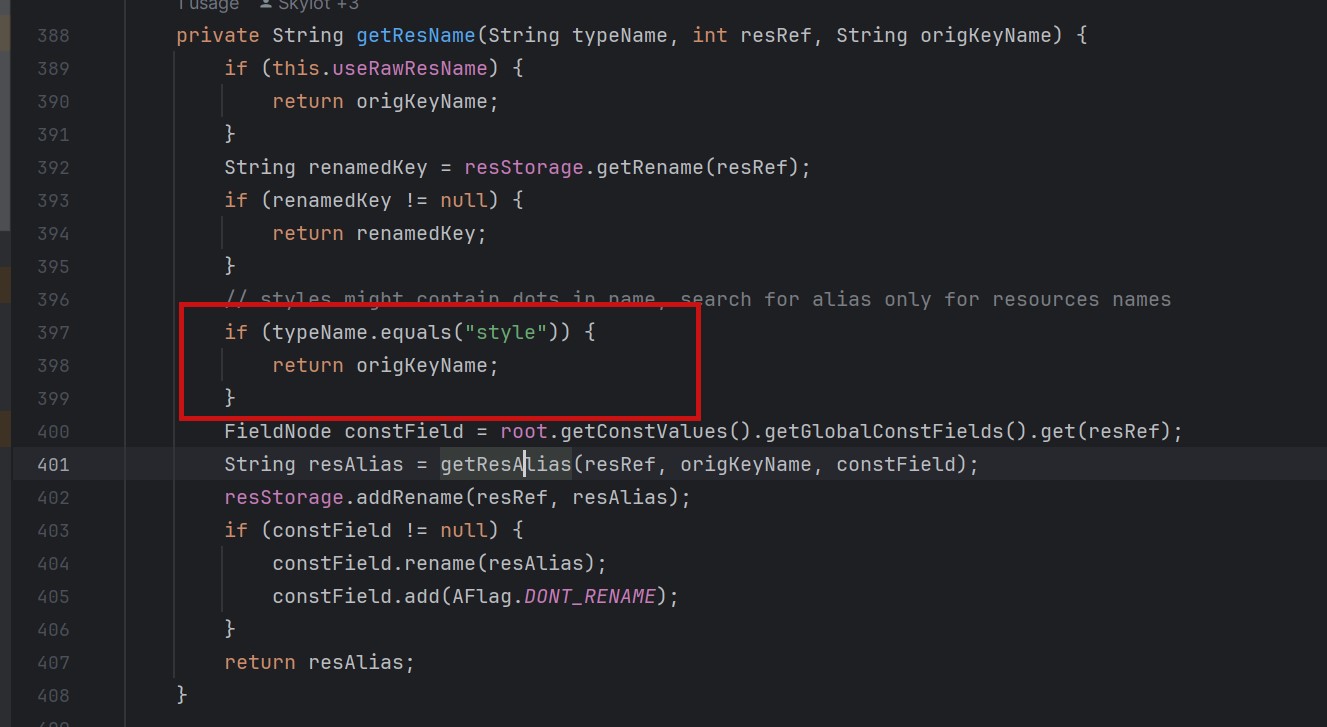 so our goal is to take a malicious file that was originally of type raw, modify its type to style, trick jadx into #### step1 create an android project using androidstudio and create a raw folder with the name attack_file_sayhiiiiiiiiiiiii, it doesn't matter what the content is! 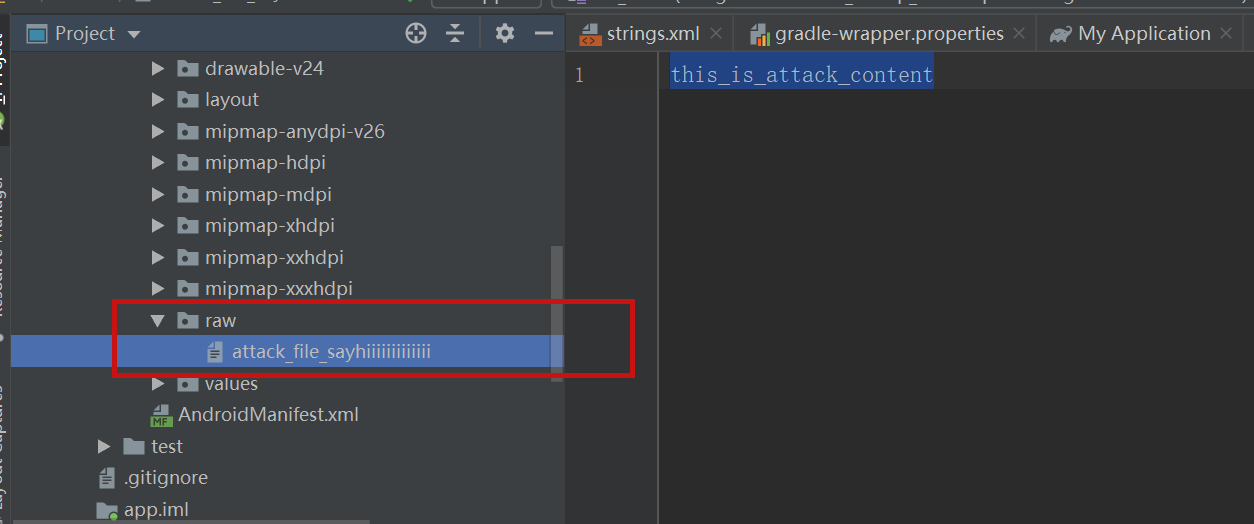 generate an initial APK #### s...
The five intelligence sources that power social engineering scams.
By Deeba Ahmed Shadowboxing in Search Results: Tuta Mail De-ranked and Disappearing on Google! This is a post from HackRead.com Read the original post: Tuta Mail (Tutanota) Accuses Google of Censoring Its Search Results
At most, someone who intentionally or repeatedly shares information on their social platform that’s misleading or downright false may have their account blocked, suspended or deleted.
A new Android trojan called SoumniBot has been detected in the wild targeting users in South Korea by leveraging weaknesses in the manifest extraction and parsing procedure. The malware is "notable for an unconventional approach to evading analysis and detection, namely obfuscation of the Android manifest," Kaspersky researcher Dmitry Kalinin said in a technical analysis.
**What type of information could be disclosed by this vulnerability?** The type of information that could be disclosed if an attacker successfully exploited this vulnerability is sensitive information.
"Kapeka" and "Fuxnet" are the latest examples of malware to emerge from the long-standing conflict between the two countries.
Ubuntu Security Notice 6726-3 - Pratyush Yadav discovered that the Xen network backend implementation in the Linux kernel did not properly handle zero length data request, leading to a null pointer dereference vulnerability. An attacker in a guest VM could possibly use this to cause a denial of service. It was discovered that the IPv6 implementation of the Linux kernel did not properly manage route cache memory usage. A remote attacker could use this to cause a denial of service.