Tag
#sql
Versions of the package mysql2 before 3.9.7 are vulnerable to Arbitrary Code Injection due to improper sanitization of the timezone parameter in the readCodeFor function by calling a native MySQL Server date/time function.
### Summary Using a version of `sqlparse` that has a security vulnerability and no way to update in current version of dbt core. Snyk recommends using `sqlparse==0.5` but this causes a conflict with dbt. Snyk states the issues is a recursion error: `SNYK-PYTHON-SQLPARSE-6615674`. ### Details Dependency conflict error message: ```sh The conflict is caused by: The user requested sqlparse==0.5 dbt-core 1.7.10 depends on sqlparse<0.5 and >=0.2.3 ``` Resolution was to pin `sqlparse >=0.5.0, <0.6.0` in `dbt-core`, patched in 1.6.13 and 1.7.13. ### PoC From Snyk: ```python import sqlparse sqlparse.parse('[' * 10000 + ']' * 10000) ``` ### Impact Snyk classifies it as high 7.5/10. ### Patches The bug has been fixed in [dbt-core v1.6.13](https://github.com/dbt-labs/dbt-core/releases/tag/v1.6.13) and [dbt-core v1.7.13](https://github.com/dbt-labs/dbt-core/releases/tag/v1.7.13). ### Mitigations Bump `dbt-core` 1.6 and 1.7 dependencies to 1.6.13 and 1.7.13 respectively
### Summary Get a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0 ### Details in file `api_functions.php`, line 307 for function list_devices ```php $order = $request->get('order'); $type = $request->get('type'); $query = $request->get('query'); $param = []; if (empty($order)) { $order = 'hostname'; } if (stristr($order, ' desc') === false && stristr($order, ' asc') === false) { $order = 'd.`' . $order . '` ASC'; } /* ... */ $devices = []; $dev_query = "SELECT $select FROM `devices` AS d $join WHERE $sql GROUP BY d.`hostname` ORDER BY $order"; foreach (dbFetchRows($dev_query, $param) as $device) { ``` The "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in...
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 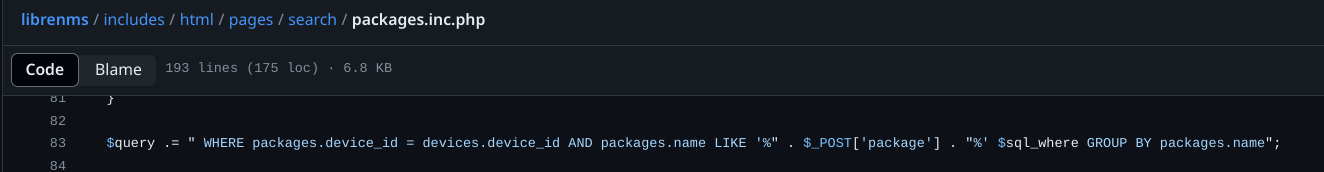 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
Users will need to download the latest version of Ivanti's Avalanche to apply fixes for all of the bugs.
pgAdmin versions 8.3 and below have a path traversal vulnerability within their session management logic that can allow a pickled file to be loaded from an arbitrary location. This can be used to load a malicious, serialized Python object to execute code within the context of the target application. This exploit supports two techniques by which the payload can be loaded, depending on whether or not credentials are specified. If valid credentials are provided, Metasploit will login to pgAdmin and upload a payload object using pgAdmin's file management plugin. Once uploaded, this payload is executed via the path traversal before being deleted using the file management plugin. This technique works for both Linux and Windows targets. If no credentials are provided, Metasploit will start an SMB server and attempt to trigger loading the payload via a UNC path. This technique only works for Windows targets. For Windows 10 v1709 (Redstone 3) and later, it also requires that insecure outbound g...
Cybersecurity researchers have discovered a new campaign that's exploiting a recently disclosed security flaw in Fortinet FortiClient EMS devices to deliver ScreenConnect and Metasploit Powerfun payloads. The activity entails the exploitation of CVE-2023-48788 (CVSS score: 9.3), a critical SQL injection flaw that could permit an unauthenticated attacker to execute unauthorized code or
Centreon version 23.10-1.el8 suffers from a remote authenticated SQL injection vulnerability.
### Summary Passing a heavily nested list to sqlparse.parse() leads to a Denial of Service due to RecursionError. ### Details + PoC Running the following code will raise Maximum recursion limit exceeded exception: ```py import sqlparse sqlparse.parse('[' * 10000 + ']' * 10000) ``` We expect a traceback of RecursionError: ```py Traceback (most recent call last): File "trigger_sqlparse_nested_list.py", line 3, in <module> sqlparse.parse('[' * 10000 + ']' * 10000) File "/home/uriya/.local/lib/python3.10/site-packages/sqlparse/__init__.py", line 30, in parse return tuple(parsestream(sql, encoding)) File "/home/uriya/.local/lib/python3.10/site-packages/sqlparse/engine/filter_stack.py", line 36, in run stmt = grouping.group(stmt) File "/home/uriya/.local/lib/python3.10/site-packages/sqlparse/engine/grouping.py", line 428, in group func(stmt) File "/home/uriya/.local/lib/python3.10/site-packages/sqlparse/engine/grouping.py", line 53, in group_brackets _group_mat...