Tag
#webkit
Every week, the cyber world reminds us that silence doesn’t mean safety. Attacks often begin quietly — one unpatched flaw, one overlooked credential, one backup left unencrypted. By the time alarms sound, the damage is done. This week’s edition looks at how attackers are changing the game — linking different flaws, working together across borders, and even turning trusted tools into weapons.
With the mercenary spyware industry booming, Apple VP Ivan Krstić tells WIRED that the company is also offering bonuses that could bring the max total reward for iPhone exploits to $5 million.
Apple on Monday backported fixes for a recently patched security flaw that has been actively exploited in the wild. The vulnerability in question is CVE-2025-43300 (CVSS score: 8.8), an out-of-bounds write issue in the ImageIO component that could result in memory corruption when processing a malicious image file. "Apple is aware of a report that this issue may have been exploited in an
### Summary An arbitrary file read vulnerability in the `chatId` parameter supplied to both the `/api/v1/get-upload-file` and `/api/v1/openai-assistants-file/download` endpoints allows unauthenticated users to read unintended files on the local filesystem. In the default Flowise configuration this allows reading of the local sqlite db and subsequent compromise of all database content. ### Details Both the `/api/v1/get-upload-file` and `/api/v1/openai-assistants-file/download` endpoints accept the `chatId` parameter and pass this to a subsequent call to streamStorageFile(). ``` const chatflowId = req.query.chatflowId as string const chatId = req.query.chatId as string const fileName = req.query.fileName as string ... const fileStream = await streamStorageFile(chatflowId, chatId, fileName, orgId) ``` While streamStorageFile validates that the chatflowId is a UUID and strips traversal sequences from fileName, it performs no validation of chatId. ``` // Validate chatflowId ...
### Summary It has been discovered that the middleware functionality in Hoverfly is vulnerable to command injection through its `/api/v2/hoverfly/middleware` endpoint due to insufficient validation and sanitization in user input. ### Details The vulnerability exists in the middleware management API endpoint `/api/v2/hoverfly/middleware`. This issue is born due to combination of three code level flaws: 1. Insufficient Input Validation in [middleware.go line 94-96](https://github.com/SpectoLabs/hoverfly/blob/master/core/middleware/middleware.go#L93): ``` func (this *Middleware) SetBinary(binary string) error { this.Binary = binary // No validation of binary parameter here return nil } ``` 2. Unsafe Command Execution in [local_middleware.go line 14-19](https://github.com/SpectoLabs/hoverfly/blob/master/core/middleware/local_middleware.go#L13): ``` var middlewareCommand *exec.Cmd if this.Script == nil { middlewareCommand = exec.Command(this.Binary) // User-controlled b...
A list of topics we covered in the week of July 28 to August 3 of 2025
Apple has released important security updates for iOS and iPadOS patching 29 vulnerabilities, mostly in WebKit.
### Summary A log injection vulnerability was identified in `pyload` in API `/json/add_package`. This vulnerability allows user with add packages permission to inject arbitrary messages into the logs gathered by `pyload`. ### Details `pyload` will generate a log entry when creating new package using API `/json/add_package`. This entry will be in the form of `Added package 'NAME_OF_PACKAGE' containing 'NUMBER_OF_LINKS' links`. However, when supplied with the name of new package containing a newline, this newline is not properly escaped. Newlines are also the delimiter between log entries. This allows the attacker to inject new log entries into the log file. ### PoC Run `pyload` in the default configuration by running the following command ``` pyload ``` We can now sign in as the pyload user who at least have add packages permissions. In my example, I will use the admin account to demonstrate this vulnerability. Now as an admin user, view the logs at `http://localhost:8000/logs` <img wi...
# Summary The Dolibarr backend provides the function of adding Menu, and supports setting permissions for the added Menu: 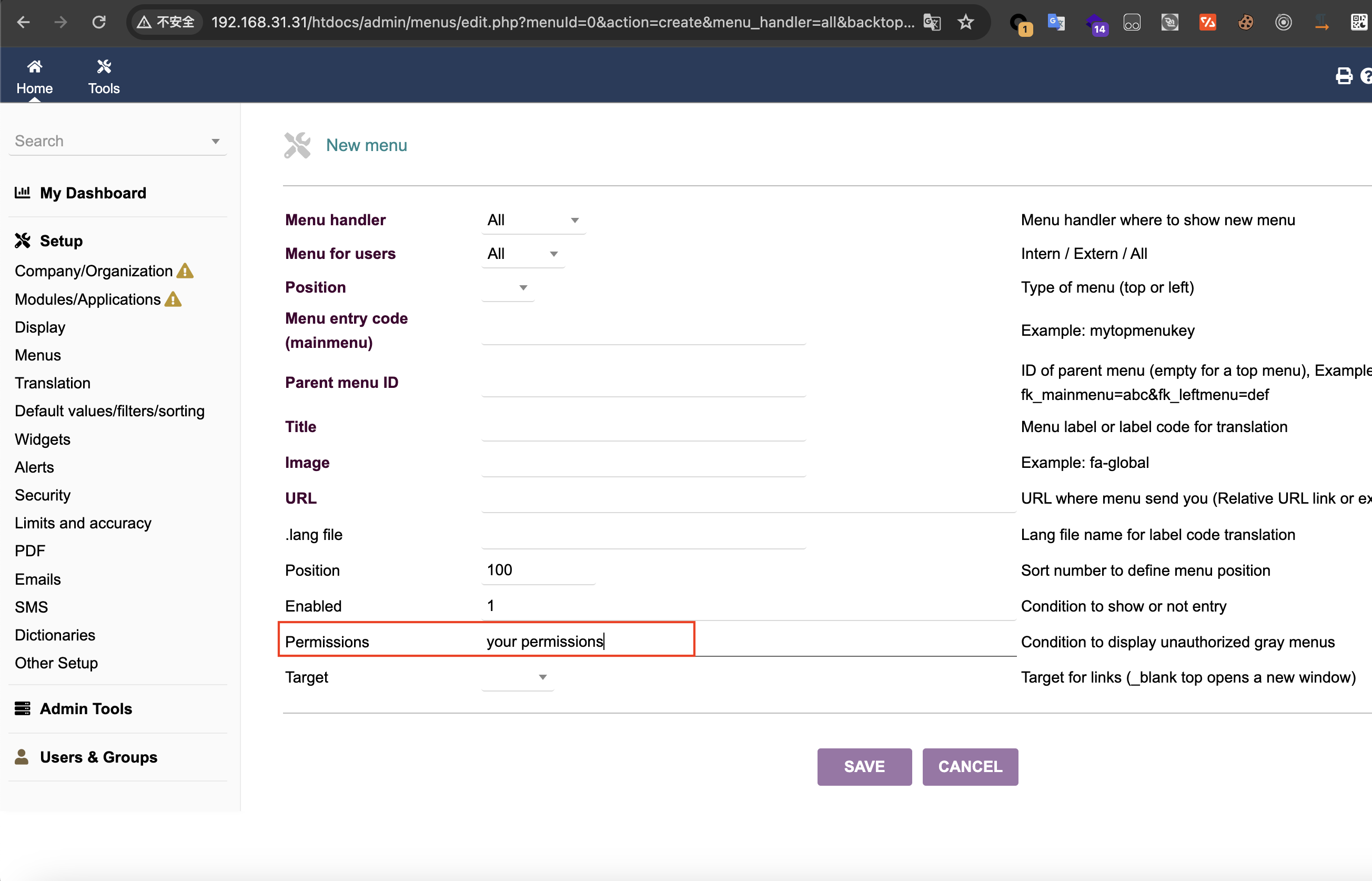 This is the trigger point of the vulnerability. The submitted permission can be php code, and it will be executed when viewing the created Menu: - htdocs/admin/menus/edit.php 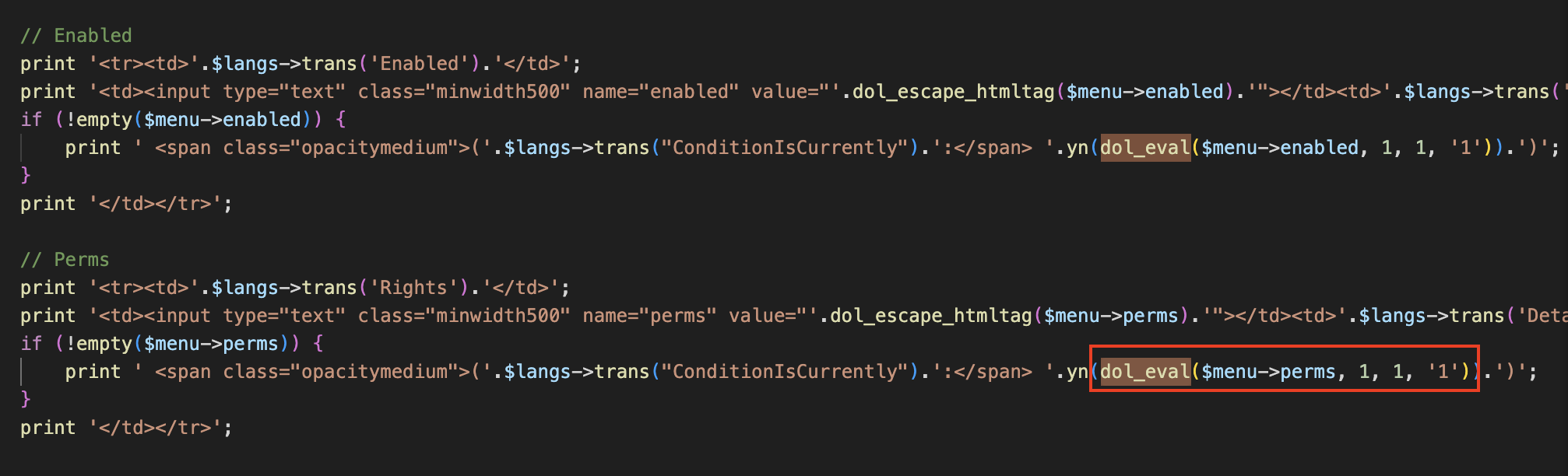 As you can see, in edit.php, if the created menu is set to `$menu->perms`, the `dol_eval()` method will be called. Following the `dol_eval()` method, we can see that it will filter the dangerous php functions in `$menu->perms` through the blacklist set in `$forbiddenphpfunctions`: 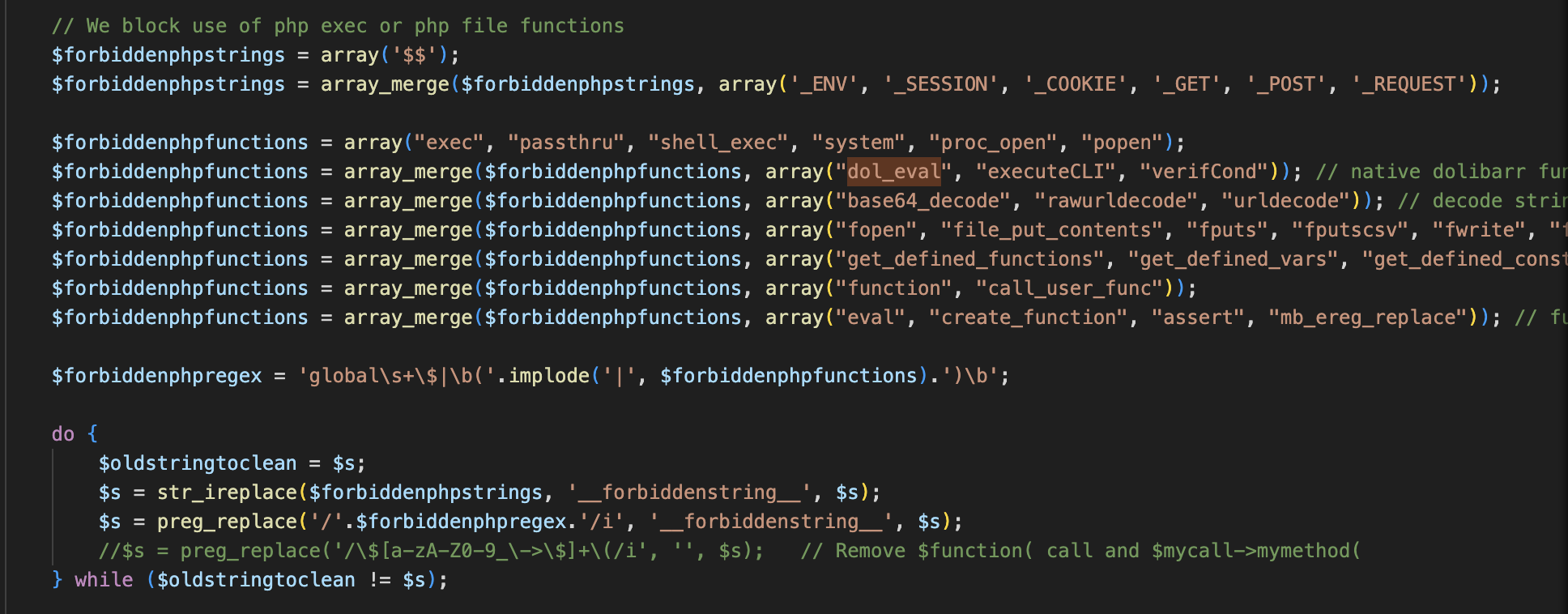 However, the blacklist here is not comprehensive. For example, the `include_once` and `require_once` functions can easily pass the bla...
### Summary File Browser’s authentication system issues long-lived JWT tokens that remain valid even after the user logs out. Please refer to the CWE's listed in this report for further reference and system standards. In summary, the main issue is: - Tokens remain valid after logout (session replay attacks) In this report, I used docker as the documentation instruct: ``` docker run \ -v filebrowser_data:/srv \ -v filebrowser_database:/database \ -v filebrowser_config:/config \ -p 8080:80 \ filebrowser/filebrowser ``` ### Details **Issue: Tokens remain valid after logout (session replay attacks)** After logging in and receiving a JWT token, the user can explicitly "log out." However, this action does not invalidate the issued JWT. Any captured token can be replayed post-logout until it expires naturally. The backend does not track active sessions or invalidate existing tokens on logout. Login request: ``` POST /api/login HTTP/1.1 Host: machine.local:8090 Cont...