Source
ghsa
Mattermost fails to properly check a redirect URL parameter allowing for an open redirect was possible when the user clicked "Back to Mattermost" after providing a invalid custom url scheme in /oauth/{service}/mobile_login?redirect_to=
Mattermost fails to check if hardened mode is enabled when overriding the username and/or the icon when posting a post. If settings allowed integrations to override the username and profile picture when posting, a member could also override the username and icon when making a post even if the Hardened Mode setting was enabled
Mattermost fails to use innerText / textContent when setting the channel name in the webapp during autocomplete, allowing an attacker to inject HTML to a victim's page by create a channel name that is valid HTML. No XSS is possible though.
### Summary Google Analytics element Attribute Injection leading to XSS ### Details Since the custom status interface can set an independent Google Analytics ID and the template has not been sanitized, there is an attribute injection vulnerability here, which can lead to XSS attacks. 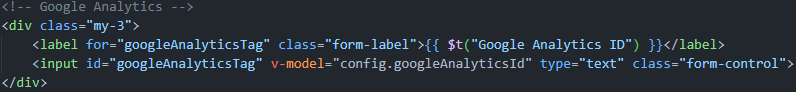 ### PoC 1. Run the latest version of the louislam/uptime-kuma container and initialize the account password. 2. Create a new status page. 3. Edit the status page and change the Google Analytics ID to following payload(it only works for firefox. Any attribute can be injected, but this seems the most intuitive): ``` 123123" onafterscriptexecute=alert(window.name+1),eval(window.name) a="x ``` 4. Click Save and return to the interface. XSS occurs. screenshots:  ![9d0603e634fb7da2e83a0a...
With this notification I would like to inform about a DoS vector in the Ethereum ABI decoder. We have not yet found a way to exploit this with high impact, still the bug could potentially lead to a DoS in server systems. Feel free to ask about an extension of the embargo period. Trail of Bits is informing you and other vendors as a community service, and so we do not seek a bug bounty on these issues. ## BUG DESCRIPTION Parsers must be written in a robust way, which avoids for example unrecoverable crashes, misinterpretation, hangs, or excessive resource consumption. The recent news about the aCropalypse bug also highlights that more subtle bugs like blind spots in file formats can lead to serious implications. Sometimes the specifications are at fault and sometimes the implementations. In the case of the Ethereum ABI, I have to blame the specification more than the vulnerable implementations. The specification allows zero-sized-types (ZST), which can cause denial-of-service upon...
The privilege escalation is based on a missing check if the user is authenticated based on the `TokenReview` result. All the clusters running with the `anonymous-auth` Kubernetes API Server setting disable (set to `false`) are affected since it would be possible to bypass the token review mechanism, interacting with the upper Kubernetes API Server. # PoC Start a KinD cluster with the `anonymous-auth` value to `false`. If it is true, it uses anonymous permissions which are very limited by default ```yaml kind: Cluster apiVersion: kind.x-k8s.io/v1alpha4 nodes: - role: control-plane kubeadmConfigPatches: - | kind: ClusterConfiguration apiServer: extraArgs: anonymous-auth: "false" ``` Install `capsule` and `capsule-proxy` ``` k port-forward svc/capsule-proxy 9001 Forwarding from 127.0.0.1:9001 -> 9001 Forwarding from [::1]:9001 -> 9001 Handling connection for 9001 ``` Then query the proxy ``` curl -g -k -H 'Authorization: Bearer f' -X 'GET' 'http...
A SQL injection vulnerability in Meshery before 0.6.179 allows a remote attacker to obtain sensitive information and execute arbitrary code via the order parameter.
Exposure of Sensitive Information to an Unauthorized Actor vulnerability in Apache DolphinScheduler. The information exposed to unauthorized actors may include sensitive data such as database credentials. Users who can't upgrade to the fixed version can also set environment variable `MANAGEMENT_ENDPOINTS_WEB_EXPOSURE_INCLUDE=health,metrics,prometheus` to workaround this, or add the following section in the `application.yaml` file ``` management: endpoints: web: exposure: include: health,metrics,prometheus ``` This issue affects Apache DolphinScheduler: from 3.0.0 before 3.0.2. Users are recommended to upgrade to version 3.0.2, which fixes the issue.
The openssl (aka node-openssl) NPM package through 2.0.0 was characterized as "a nonsense wrapper with no real purpose" by its author, and accepts an opts argument that contains a verb field (used for command execution). NOTE: This vulnerability only affects products that are no longer supported by the maintainer.
Bouncy Castle for Java before 1.73 contains a potential Denial of Service (DoS) issue within the Bouncy Castle org.bouncycastle.openssl.PEMParser class. This class parses OpenSSL PEM encoded streams containing X.509 certificates, PKCS8 encoded keys, and PKCS7 objects. Parsing a file that has crafted ASN.1 data through the PEMParser causes an OutOfMemoryError, which can enable a denial of service attack.