Tag
#git
The git hook feature in Gitea 1.1.0 through 1.12.5 allows for authenticated remote code execution.
### Impact A bug was found in Moby (Docker Engine) where containers were incorrectly started with non-empty inheritable Linux process capabilities, creating an atypical Linux environment and enabling programs with inheritable file capabilities to elevate those capabilities to the permitted set during `execve(2)`. Normally, when executable programs have specified permitted file capabilities, otherwise unprivileged users and processes can execute those programs and gain the specified file capabilities up to the bounding set. Due to this bug, containers which included executable programs with inheritable file capabilities allowed otherwise unprivileged users and processes to additionally gain these inheritable file capabilities up to the container's bounding set. Containers which use Linux users and groups to perform privilege separation inside the container are most directly impacted. This bug did not affect the container security sandbox as the inheritable set never contained more ...
### Observations The Hoppscotch desktop app takes multiple precautions to be secure against arbitrary JavaScript and system command execution. It does not render user-controlled HTML or Markdown, uses Tauri instead of Electron, and sandboxes pre-request scripts with a simple yet secure implementation using web workers. Unfortunately, web workers are not available in a pure Node.js application like Hoppscotch CLI. That is why the [@hoppscotch/js-sandbox](https://github.com/hoppscotch/hoppscotch/tree/main/packages/hoppscotch-js-sandbox) package also provides a Javascript sandbox that uses the Node.js `vm` module. However, the `vm` module is not safe for sandboxing untrusted Javascript code, as stated [in the documentation](https://nodejs.org/api/vm.html#vm-executing-javascript). This is because [code inside the vm context can break out](https://thegoodhacker.com/posts/the-unsecure-node-vm-module/) if it can get a hold of any reference to an object created outside of the vm. In the cas...
### Summary Get a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0 ### Details in file `api_functions.php`, line 307 for function list_devices ```php $order = $request->get('order'); $type = $request->get('type'); $query = $request->get('query'); $param = []; if (empty($order)) { $order = 'hostname'; } if (stristr($order, ' desc') === false && stristr($order, ' asc') === false) { $order = 'd.`' . $order . '` ASC'; } /* ... */ $devices = []; $dev_query = "SELECT $select FROM `devices` AS d $join WHERE $sql GROUP BY d.`hostname` ORDER BY $order"; foreach (dbFetchRows($dev_query, $param) as $device) { ``` The "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in...
### Summary There is improper sanitization on Service template name which is reflecting in delete button onclick event. This value can be modified and crafted as any other javascript code. ### Vulnerable Code https://github.com/librenms/librenms/blob/a61c11db7e8ef6a437ab55741658be2be7d14d34/app/Http/Controllers/ServiceTemplateController.php#L67C23-L67C23 Above is vulnerable code line which needs to be properly sanitized ### PoC 1. Go to /services/templates 2. Enter name as `testing', '14', 'http://172.105.62.194:8000/services/templates/14');alert(1);//` 3. Submit it and try to delete it, you will see popup If you inspect element on delete button, you will notice this:- <img width="748" alt="Screenshot 2023-11-23 at 9 30 24 PM" src="https://user-images.githubusercontent.com/31764504/285260018-7672a93d-e29b-4444-8057-e6ffcb8dabfc.png"> ### Impact Cross site scripting can lead to cookie stealing or an attacker can execute any other feature using this feature.
### Summary SQL injection vulnerability in POST /search/search=packages in LibreNMS 24.3.0 allows a user with global read privileges to execute SQL commands via the package parameter. ### Details There is a lack of hygiene of data coming from the user in line 83 of the file librenms/includes/html/pages/search/packages.inc.php 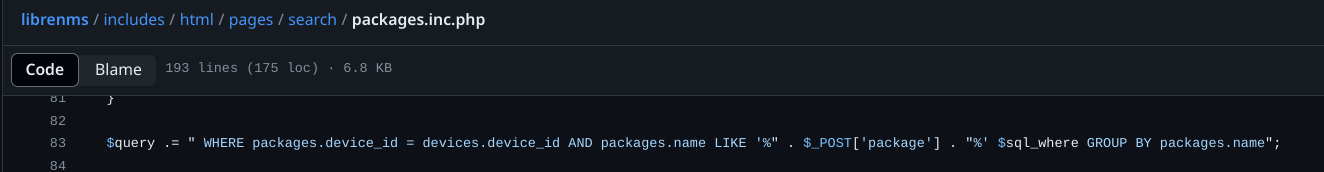 ### PoC https://doc.clickup.com/9013166444/p/h/8ckm0bc-53/16811991bb5fff6 ### Impact With this vulnerability, we can exploit a SQL injection time based vulnerability to extract all data from the database, such as administrator credentials
### Impact Under very specific conditions changes to a users groups may not have the expected results. The specific conditions are: * The file authentication backend is being used. * The [watch](https://www.authelia.com/configuration/first-factor/file/#watch) option is set to true. * The [refresh_interval](https://www.authelia.com/configuration/first-factor/introduction/#refresh_interval) is configured to a non-disabled value. * The users groups are adjusted by an administrator. * The user attempts to access a resource that their groups previously had access to but their new groups do not have access to. When these conditions are met administrators may find the changes are not taken into account by access control for longer than expected periods. While this may not necessarily be a security vulnerability it's security-adjacent and because of the unexpected nature of it and our dedication to a security-first culture we feel it's important to make users aware of this behaviour utiliz...
### Impact We have identified a local privilege escalation vulnerability in Ant Media Server which allows any unprivileged operating system user account to escalate privileges to the root user account on the system. This vulnerability arises from Ant Media Server running with Java Management Extensions (JMX) enabled and authentication disabled on localhost on port 5599/TCP. This vulnerability is nearly identical to the local privilege escalation vulnerability CVE-2023-26269 identified in Apache James. Any unprivileged operating system user can connect to the JMX service running on port 5599/TCP on localhost and leverage the MLet Bean within JMX to load a remote MBean from an attacker-controlled server. This allows an attacker to execute arbitrary code within the Java process run by Ant Media Server and execute code within the context of the “antmedia” service account on the system. ### Patches 2.9.0 ### Workarounds Remote the following parameters from antmedia.service file ```-Dcom....
Authentication Bypass by Spoofing vulnerability in Apache HugeGraph-Server.This issue affects Apache HugeGraph-Server: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.
Server-Side Request Forgery (SSRF) vulnerability in Apache HugeGraph-Hubble. This issue affects Apache HugeGraph-Hubble: from 1.0.0 before 1.3.0. Users are recommended to upgrade to version 1.3.0, which fixes the issue.