Source
ghsa
### Impact Prior to the patched version, logged in users of Mautic are able to access areas of the application that they should be prevented from accessing. Users could potentially access sensitive data such as names and surnames, company names and stage names. ### Patches Update to 4.4.12 and 5.0.4 ### Workarounds No ### References https://owasp.org/www-project-top-ten/2017/A3_2017-Sensitive_Data_Exposure
### Impact Prior to the patched version, logged in users of Mautic are vulnerable to an SQL injection vulnerability in the Reports bundle. The user could retrieve and alter data like sensitive data, login, and depending on database permission the attacker can manipulate file systems. ### Patches Update to 4.4.12 or 5.0.4 ### Workarounds No ### References - https://owasp.org/www-community/attacks/SQL_Injection - https://owasp.org/www-community/attacks/Blind_SQL_Injection
### Impact Prior to the patched version, logged in users of Mautic are vulnerable to Relative Path Traversal/Arbitrary File Deletion. Regardless of the level of access the Mautic user had, they could delete files other than those in the media folders such as system files, libraries or other important files. This vulnerability exists in the implementation of the GrapesJS builder in Mautic. ### Patches Update to 4.4.12 or 5.0.4. ### Workarounds No ### References - https://cwe.mitre.org/data/definitions/23.html - https://cwe.mitre.org/data/definitions/22.html - https://attack.mitre.org/techniques/T1630/002/ ### For more information If you have any questions or comments about this advisory: Email us at [security@mautic.org](mailto:security@mautic.org)
There is a potential vulnerability in Traefik managing requests with `Content-length` and no `body` . Sending a `GET` request to any Traefik endpoint with the `Content-length` request header results in an indefinite hang with the default configuration. This vulnerability can be exploited by attackers to induce a denial of service. ## Patches - https://github.com/traefik/traefik/releases/tag/v2.11.2 - https://github.com/traefik/traefik/releases/tag/v3.0.0-rc5 ## Workarounds For affected versions, this vulnerability can be mitigated by configuring the [readTimeout](https://doc.traefik.io/traefik/routing/entrypoints/#respondingtimeouts) option. ## For more information If you have any questions or comments about this advisory, please [open an issue](https://github.com/traefik/traefik/issues).
Insertion of Sensitive Information into Log File vulnerability in the Apache Solr Operator. This issue affects all versions of the Apache Solr Operator from 0.3.0 through 0.8.0. When asked to bootstrap Solr security, the operator will enable basic authentication and create several accounts for accessing Solr: including the "solr" and "admin" accounts for use by end-users, and a "k8s-oper" account which the operator uses for its own requests to Solr. One common source of these operator requests is healthchecks: liveness, readiness, and startup probes are all used to determine Solr's health and ability to receive traffic. By default, the operator configures the Solr APIs used for these probes to be exempt from authentication, but users may specifically request that authentication be required on probe endpoints as well. Whenever one of these probes would fail, if authentication was in use, the Solr Operator would create a Kubernetes "event" containing the username and password of the "k...
Cross Site Scripting vulnerability in tiagorlampert CHAOS v.5.0.1 allows a remote attacker to escalate privileges via the sendCommandHandler function in the handler.go component.
An issue in OpenStack magnum yoga-eom version allows a remote attacker to execute arbitrary code via the cert_manager.py. component.
### Summary Timber is vulnerable to [PHAR deserialization](https://portswigger.net/web-security/deserialization/exploiting#phar-deserialization) due to a lack of checking the input before passing it into the` file_exists()` function. If an attacker can upload files of any type to the server, he can pass in the `phar://` protocol to unserialize the uploaded file and instantiate arbitrary PHP objects. This can lead to remote code execution especially when Timber is used with frameworks with documented POP chains like Wordpress/ vulnerable developer code. ### Details The vulnerability lies in the run function within the `toJpg.php` file. The two parameters passed into it are not checked or sanitized, hence an attacker could potentially inject malicious input leading to Deserialization of Untrusted Data, allowing for remote code execution: 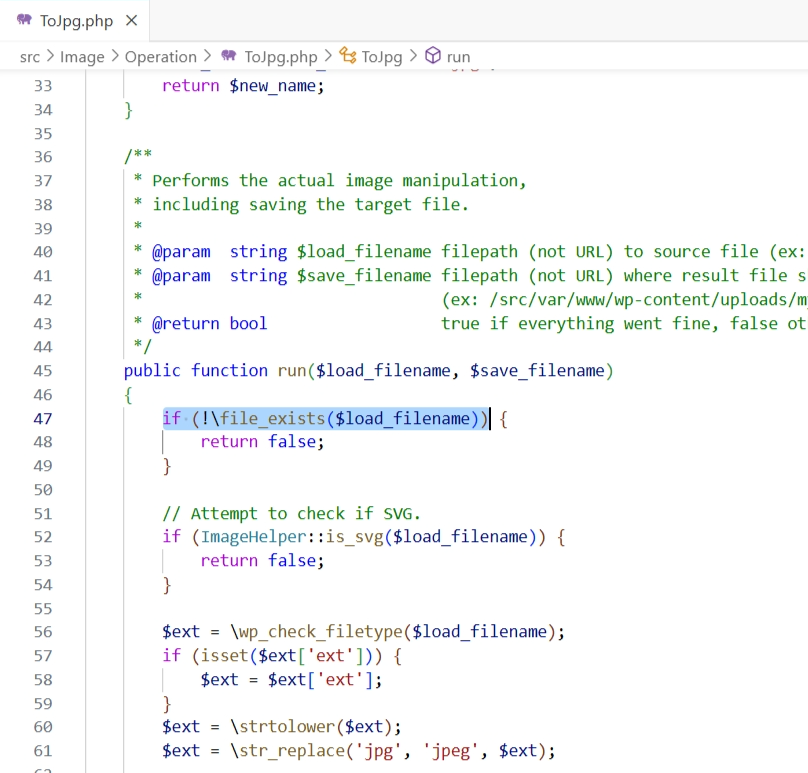 ### PoC Setup the following code in `/var/www/html`: `...
### Impact Prior to the patched version, logged in users of Mautic are vulnerable to a self XSS vulnerability in the notifications within Mautic. Users could inject malicious code into the notification when saving Dashboards. ### Patches Update to Mautic 4.4.12. ### Workarounds None ### References - https://owasp.org/www-project-top-ten/2017/A7_2017-Cross-Site_Scripting_(XSS) If you have any questions or comments about this advisory: Email us at [security@mautic.org](mailto:security@mautic.org)
While an Apache Kafka cluster is being migrated from ZooKeeper mode to KRaft mode, in some cases ACLs will not be correctly enforced. Two preconditions are needed to trigger the bug: 1. The administrator decides to remove an ACL 2. The resource associated with the removed ACL continues to have two or more other ACLs associated with it after the removal. When those two preconditions are met, Kafka will treat the resource as if it had only one ACL associated with it after the removal, rather than the two or more that would be correct. The incorrect condition is cleared by removing all brokers in ZK mode, or by adding a new ACL to the affected resource. Once the migration is completed, there is no metadata loss (the ACLs all remain). The full impact depends on the ACLs in use. If only ALLOW ACLs were configured during the migration, the impact would be limited to availability impact. if DENY ACLs were configured, the impact could include confidentiality and integrity impact depending ...